Windows LAPS: Exploring the Latest Features
Introduction
In December 2023, I made a blog about Windows LAPS for the first time. I went through how LAPS can help protect and manage the administrator passwords on our Windows devices.
Some time ago, Microsoft released some additional features for LAPS. Before you didn't have the possibility to create a custom user within your LAPS policy, now this is possible—even with randomized names across all your devices! Cool right?
Let's take a closer look at it!
Automatic Account Management
If you haven't been reading my first blog about Windows LAPS, I would highly encourage you to do so. It will give you some information on how to configure the fundamentals.
Can you guess the name of the new set of policies for LAPS? You've probably already guessed it; it's called "Automatic Account Management".
The policies can currently only be configured with the CSP option in Intune. Get ready to configure it by taking a look at the LAPS CSP.
- Navigate to the Intune portal, devices, and configuration. From here, you will have to create a new custom policy.
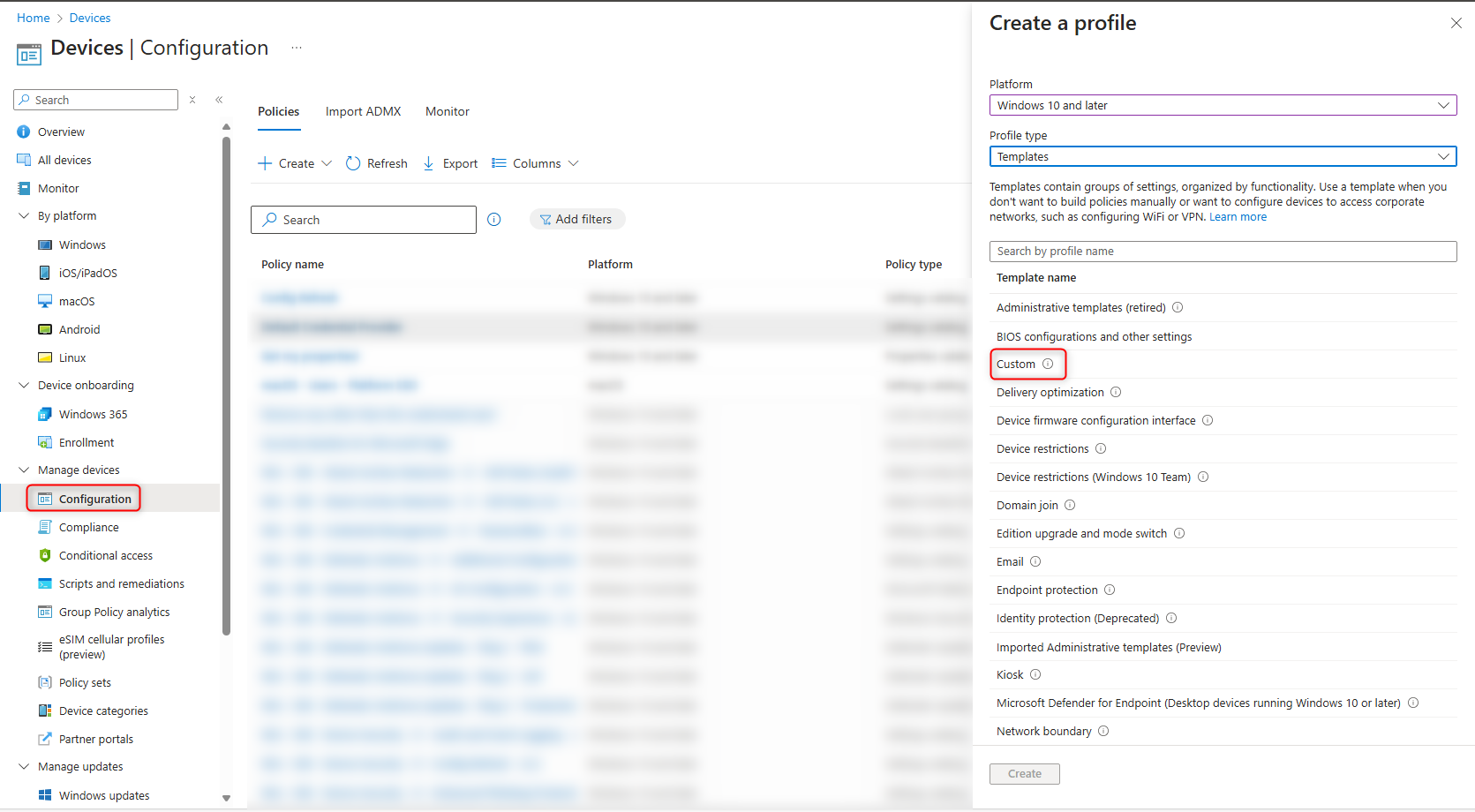
- Name your policy according to your naming convention and click next.
- Now we are ready to configure the policies. By taking a look at the LAPS CSP, you can see the policies we would have to configure.
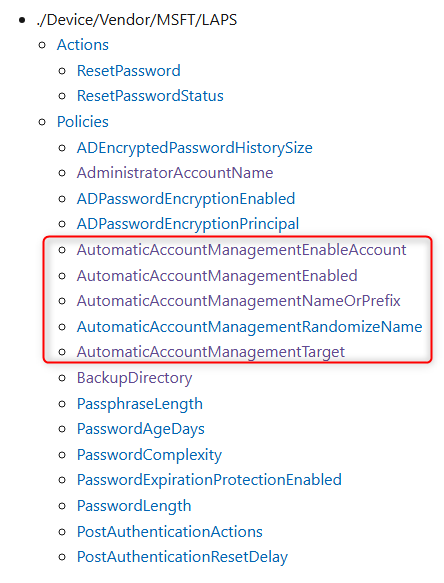
Please be aware of the following:
- AutomaticAccountManagementNameOrPrefix
- This policy is being used if you would like to create a custom user with a predefined name.
- AutomaticAccountManagementRandomizeName
- This policy is being used if you would like to create a custom user with a randomized name across your devices.
- Start off with configuring the "AutomaticAccountManagementEnabled" policy. You can decide the name and description here, but the OMA-URI, data type, and value are available on the LAPS CSP page.
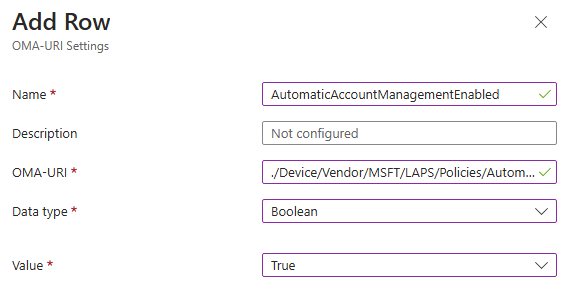
Make sure to read the properties of the policy properly; it will list format and which values are available for that specific policy.
- Configure the last policies according to their format and values from the LAPS CSP, and you will have something similar to me.
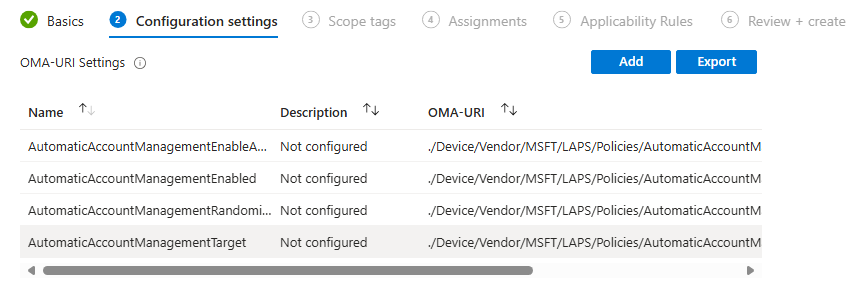
For this blog post, I will configure the randomized custom user. So I have not configured AutomaticAccountManagementNameOrPrefix.
- Now that we have configured our policies, the last thing we have to take care of is our assignments and click create!
What Should We Do With Our LAPS Policy?
One question that came to mind when I configured the "Automatic Account Management" policies the first time was "What should I do with my LAPS policy?"
It was tricky, because if you create a custom user, you would have to specify the name in your policy. However, what if my user is randomized across all my devices? Should I create a policy per device? No!
In my case, I created a user with a randomized username. The clever thing about the LAPS policy is that it knows that it needs to target that user if it exists on the device. You only have to configure the "Administrator Account Name" as "Not Configured".
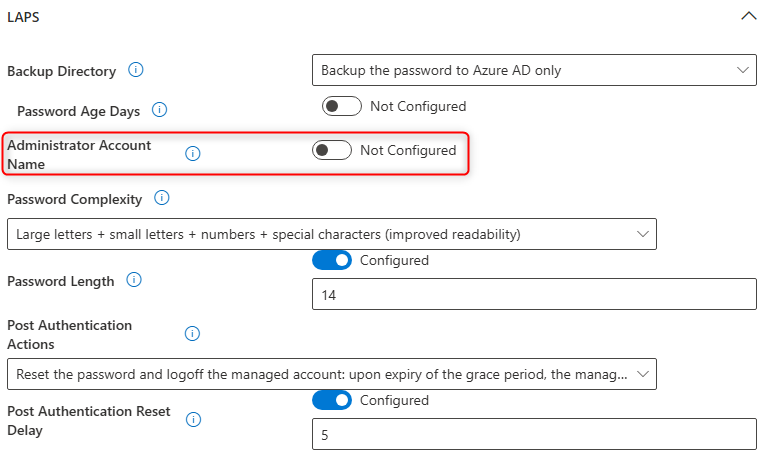
Local User Group Membership
I am thinking a lot, and another thing I was unsure about was the "Local User Group Membership" policy. This policy helps us make sure that only the users we specify are in the local administrator group with Add (Replace).
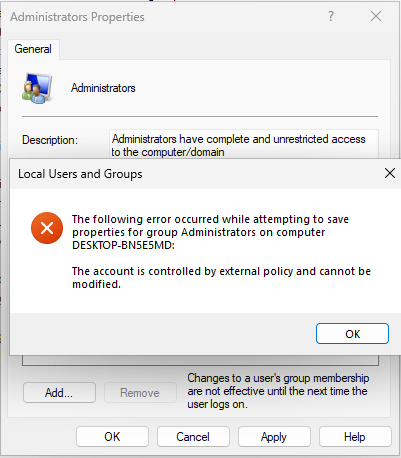
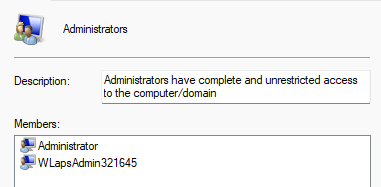
If we were using the built-in administrator or a predefined custom user, it would be easy to specify in this policy. However, it is not that easy when the user's name is randomized. I asked a good friend (Rudy Ooms), and he said: "The user created by Automatic Account Management is a protected user together with the built-in administrator."
When you are using the Add (Replace) and removing everything unless the users you specify, the built-in administrator will always stay in the group. The same goes for the user created by the "Automatic Account Management" policies. If you try to remove it manually, you will get the below error.
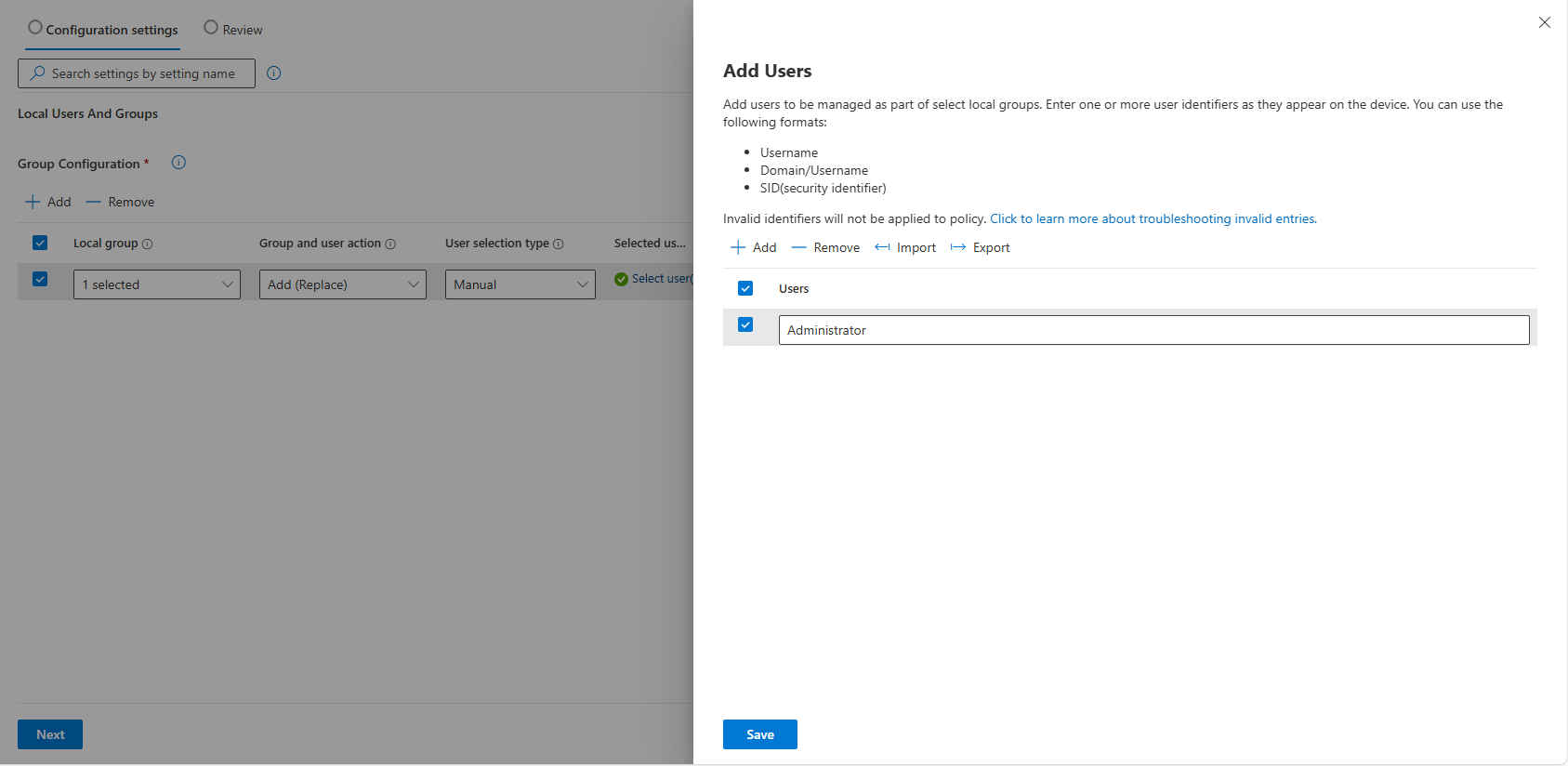
So when you are configuring the policy, you can specify the built-in administrator, and your custom user will still stay in the group.
The Experience From the Device
When the policies have been applied to the device, the user will be created and put in the local administrator group.
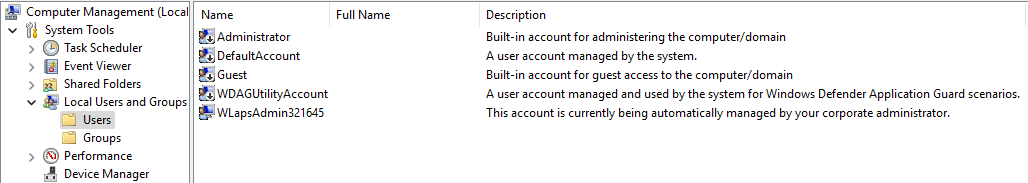
If you have seen my previous blog about Windows LAPS, you probably know where the policies are located in the registry. Head into the registry path:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Policies\LAPS
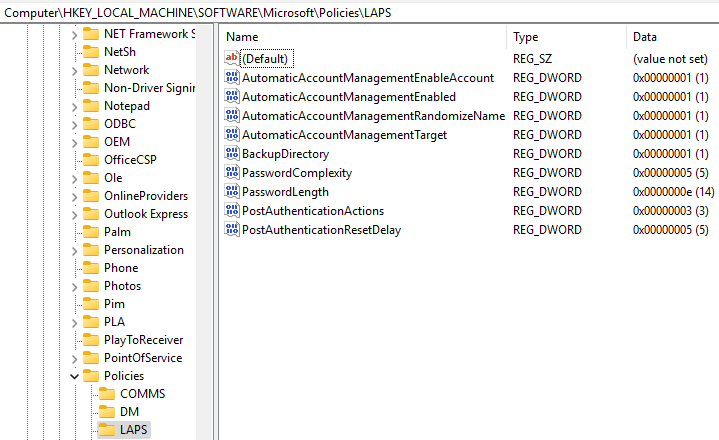
We can see that all our policies have been assigned to the device, which includes both LAPS and the "Automatic Account Management" policies.
Conclusion
Thank you for taking the time to read my blog post. I hope it gave you some insights on how the new "Automatic Account Management" policies work.
If you've been using the built-in administrator before for LAPS, I would highly recommend you disable this account with the policy called "Accounts Enable Administrator Account Status".
