Introduction to TAP
Introduction
It's important to discuss passwordless authentication as we move toward a secure and user-friendly environment.
Passwords are an attack factor for as long as they exist. Who doesn't have a mom or grandma who has a sticky note somewhere with their e-mail password?
Nowadays, Microsoft tells us to work towards passwordless authentication.
This blog is not about that journey. If you want your organization to start with it, Microsoft has an advanced deployment guide for it.
One of the methods you have available to use with passwordless is a TAP, better known as a Temporary Access Pass. TAP can be used as a temporary password for many different things, including setting up your Authenticator app or Windows Autopilot.
Enabling the TAP functionality
Before using it, we need to enable the TAP functionality in our tenant.
To do so, we need to go to the Microsoft Entra admin center > Protection > Authentication Methods > Policies.
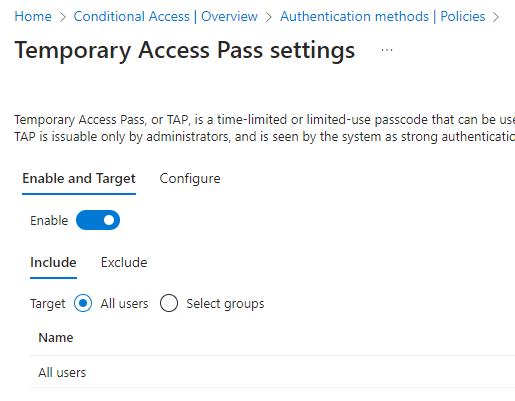
- We click on Temporary Access Pass and can enable it with one switch.
Here, we can also choose which groups to include and exclude.
- We are able to edit the general options under the Configure tab.
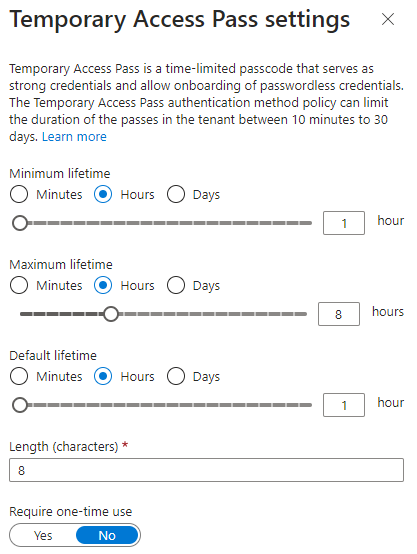
- But for now, we leave this as is. Click save and continue to the next step!
Generating the TAP for a user
We are able to use the TAP functionality now that we have enabled it.
To do so, we head to the user you want to use this with: Authentication methods > Add authentication method and select Temporary Access Pass as the method.
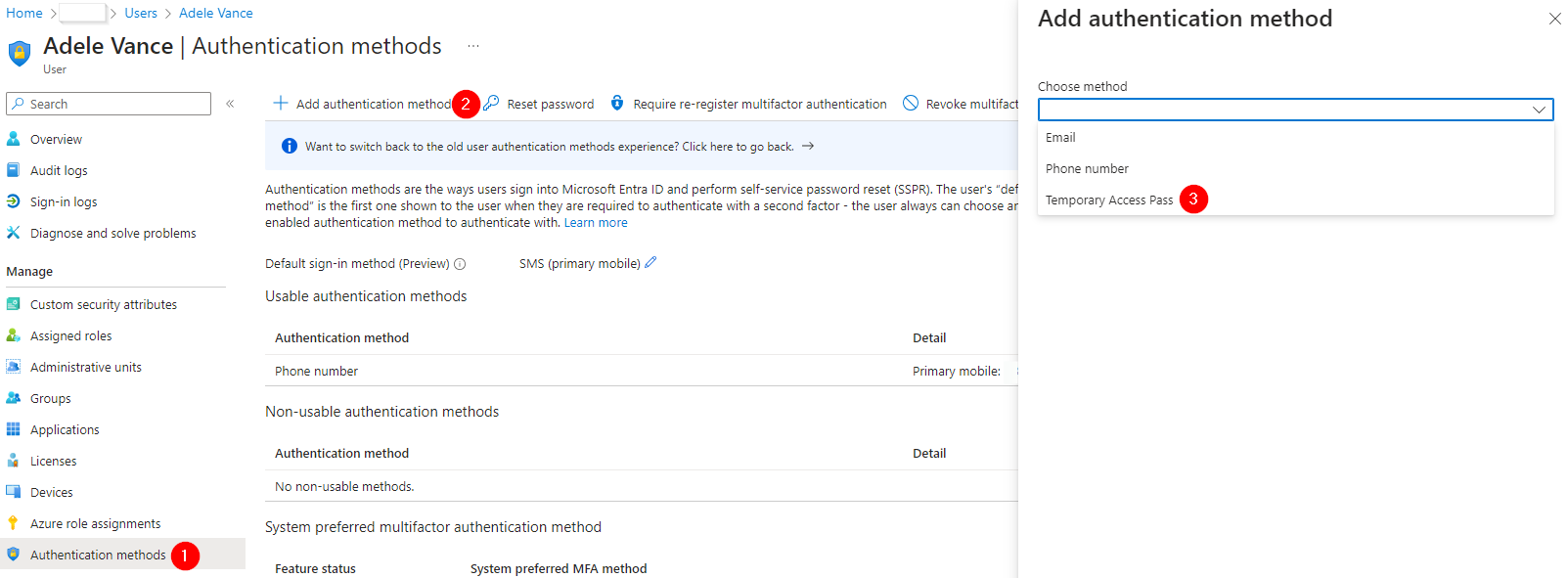
When you have chosen Temporary Access Pass as your authentication, you will see some options available.
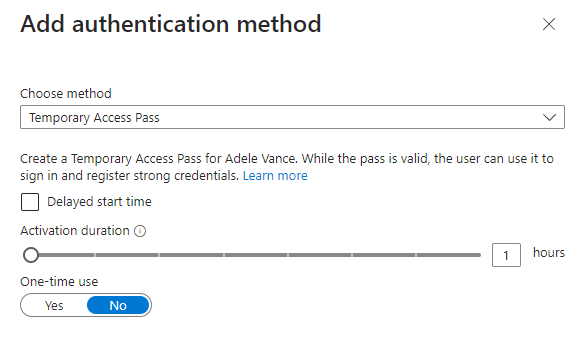
- Delayed start time: You can delay the start time by date and time. If you want to be very specific, you can modify the time zone as well.
- Activation duration: With this setting, you can specify for how long you wish to have the temporary access pass active. It can be at least an hour, and eight hours is the longest.
- One-time use: Do you wish the user to be able to use it more than once?
Once you have decided how to configure the three different settings, make sure to press add at the bottom.
It will now give you the temporary access pass, and you will be able to use it as an authentication method.
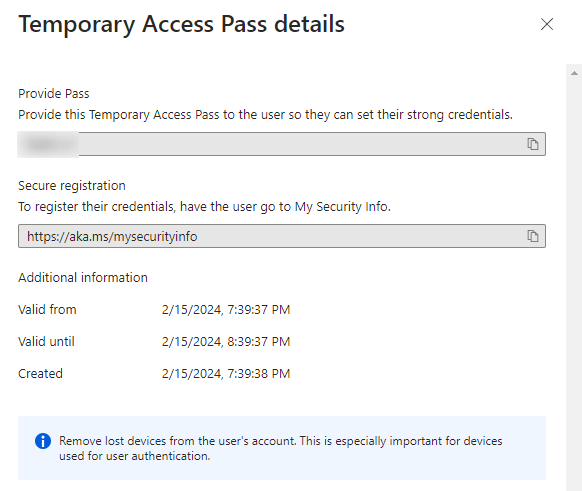
End-user experience
I have created the TAP for my user, and I would like to test it out. I have decided to login to portal.office.com and try to see what happens.
I have entered the email of the user, and it's now asking me for the TAP and not the user's password as it would normally.
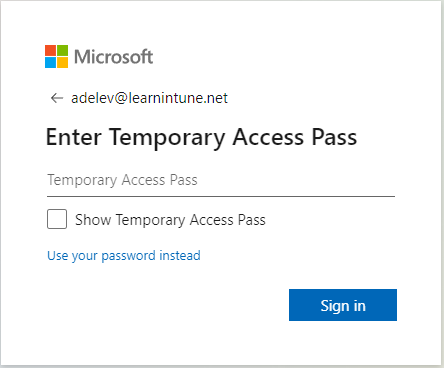
As you might see from the picture above, you also have the option to use the password instead. I will enter my TAP and see if it allows me through!
Luckily for me, it's giving me access, and I'm now able to get in to portal.office.com.
If you try to head to my sign-ins on the user account, you will also notice under security info that the temporary access pass is available as a sign-in method.
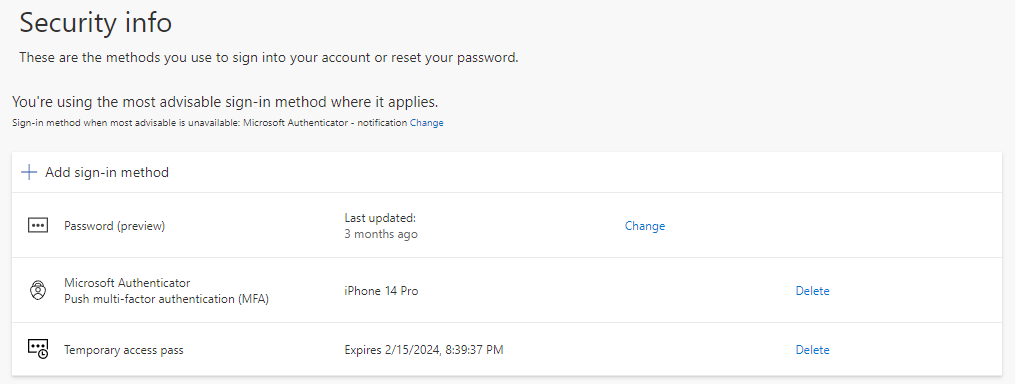
Sign-in logs
If you tried to test the TAP with me, you will notice that it doesn't ask for approval in your Microsoft Authenticator app. How can that be? So the TAP is an authentication method, exactly like the Authenticator app is.
I have taken a look at the sign-in logs for the user I tested with. It's worth mentioning that I have a conditional access policy that enforces MFA for users.
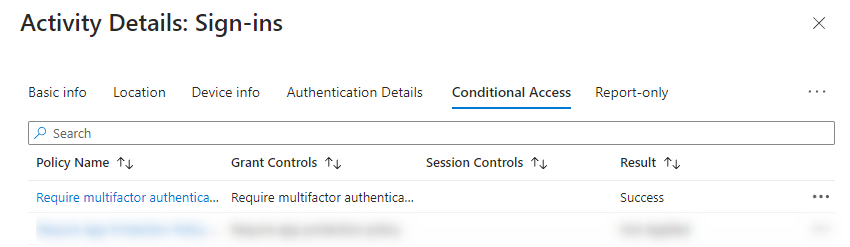
If I take a look at my sign-in logs, can I see that the login attempt was a success. If we try to take a look deeper, we can see that "require multifactor authentication" is satisfied.
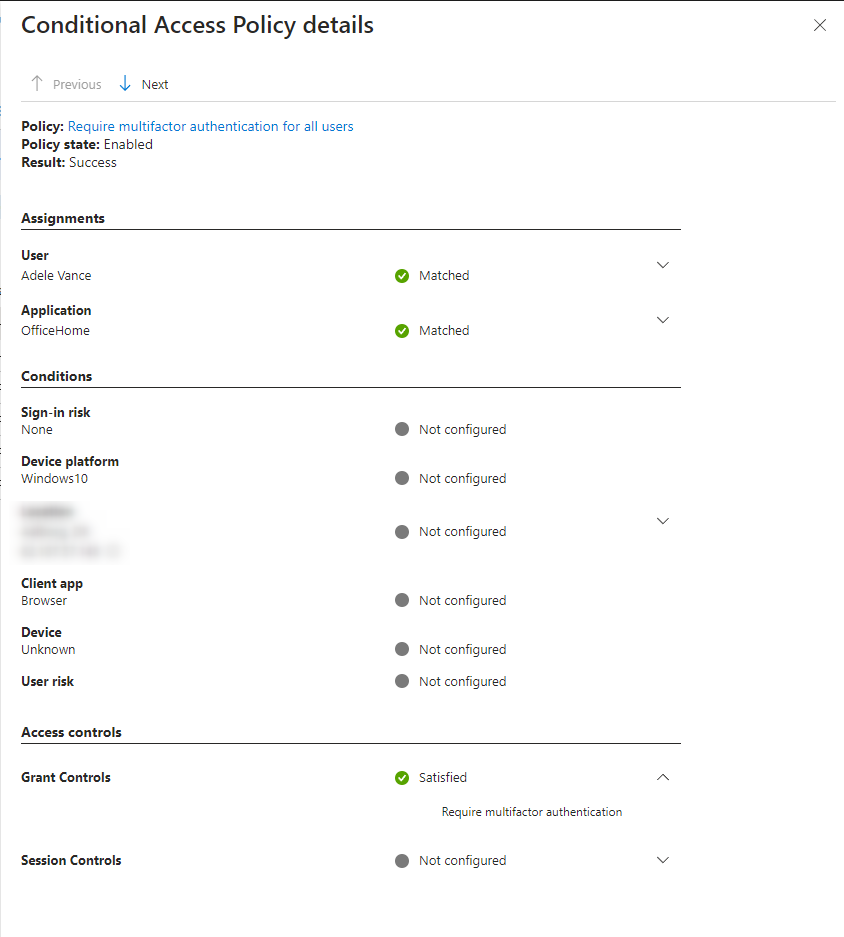
Conclusion
Thank you very much for reading this blog about TAP, it's the first out of a series of two blogs. We will try to show how easy TAP can make it for an administrator, but there is also some knowledge you have to keep in mind.

