Administrator Protection: Stay Secure!

Introduction
The new Administrator Protection feature is currently in Windows Insider preview, and from the first glance it looks promising. There are some organizations out there that cannot "just" remove local administrator rights from their users, in that case, Administrator Protection could be one of the solutions.
Administrator Protection utilizes a virtual account that is being used when you are elevating on your device. This makes sure that it's isolated from the standard account on the device.
As mentioned earlier, the Administrator Protection is currently only available in Windows Insiders versions. Keep that in mind before you start testing.
Configuration
When we are talking about the configuration of Administrator Protection, it's fairly simple. We can configure it through Microsoft Intune, Group Policy, and locally directly on the device. My favorite way to do it is, of course, through Intune.
- The first step is to jump directly into the device section of Intune.
- From here, navigate to configuration and click create new policy.
- Select Windows 10 and later and the settings catalog.
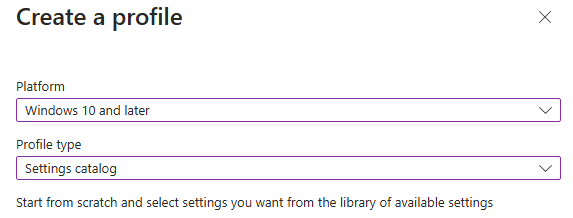
- Name your policy as you like, and click next. From here, add settings and search for "User Account Control Type Of Admin Approval Mode".
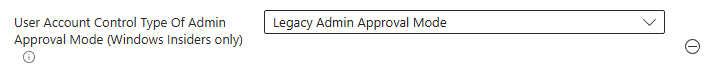
It will default choose to use "Legacy Admin Approval Mode". In order to activate Administrator Protection, we will need to switch it to "Admin Approval Mode with Administrator Protection".
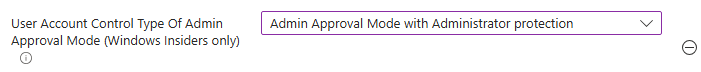
- We are not finished yet! We need to add another policy, this is the policy that decides how our UAC prompts will look. Search for "User Account Control Behavior Of The Elevation Prompt For Administrator Protection" and add the policy to your profile.

By default, this will be configured to "Prompt for credentials on the secure desktop". This can however be changed to consent only instead.
My best advice is to use the credentials, as this makes the user enter their credentials before elevating administrator rights. However, please use what works best for your organization.
- Now we are finished with configuring the settings, and the last thing you have to do is configure your assignments.
End-User Experience
Administrator Protection has now been enabled on my test device, and I want to show you how the end-user experience is. I have enabled UAC prompt behavior to consent on this test device.
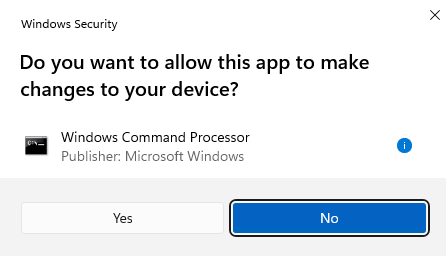
In this example, I am trying to elevate the command prompt on this device. It asks me for consent (yes/no) if I would like to allow this app to make changes to my device.
If we try to run a "whoami" in the command prompt, we can see that a new user will appear named "admin_gradyarchie". Grady Archie is my standard user, so a new user has been created just with "admin_"
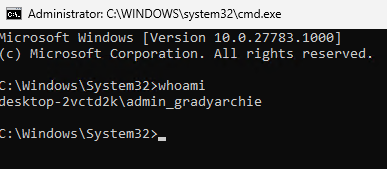
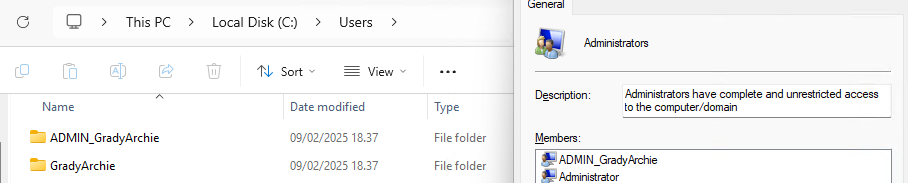
If we take a look in the "C:\Users" folder and in the administrators group, we can now see the same user as displayed in the command prompt.
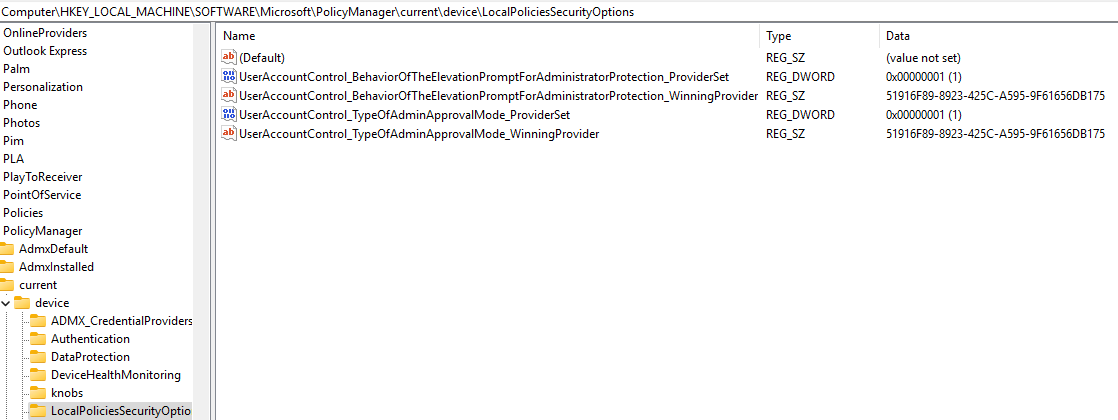
We can't do a blog about this topic without checking the registry. Navigate to the policymanager, and in there you will see Administrator Protection enabled.
Administrator Protection & Config Refresh
Have you heard about Config Refresh before? It's magic and a really nice feature that I think everyone should take a look at. Take a look at my blog about it right here.
I was wondering when playing around with Administrator Protection if Config Refresh will reinforce it if a user manually disables it through Windows Security Center. Let's try it ourselves! I have navigated to Windows Security Center, and from here we can disable Administrator Protection.
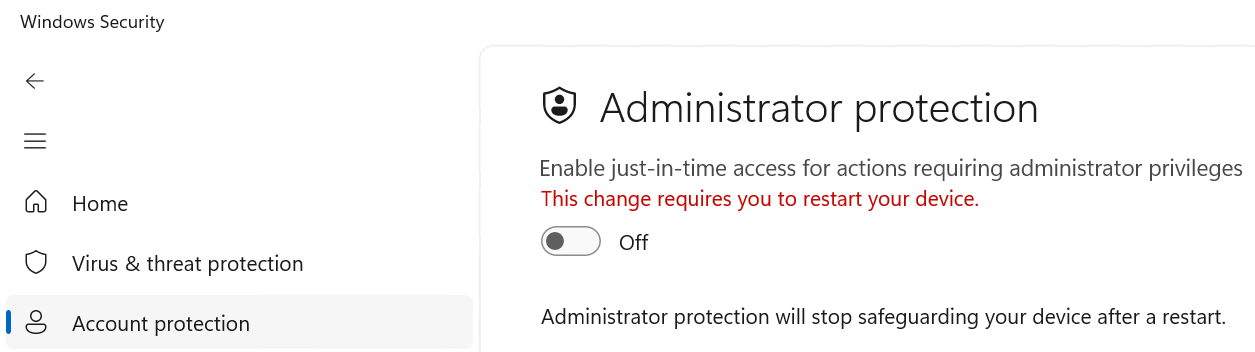
Depending on your refresh cadence for Config Refresh, you can either wait or manually run the task. I will go ahead and manually run the task.
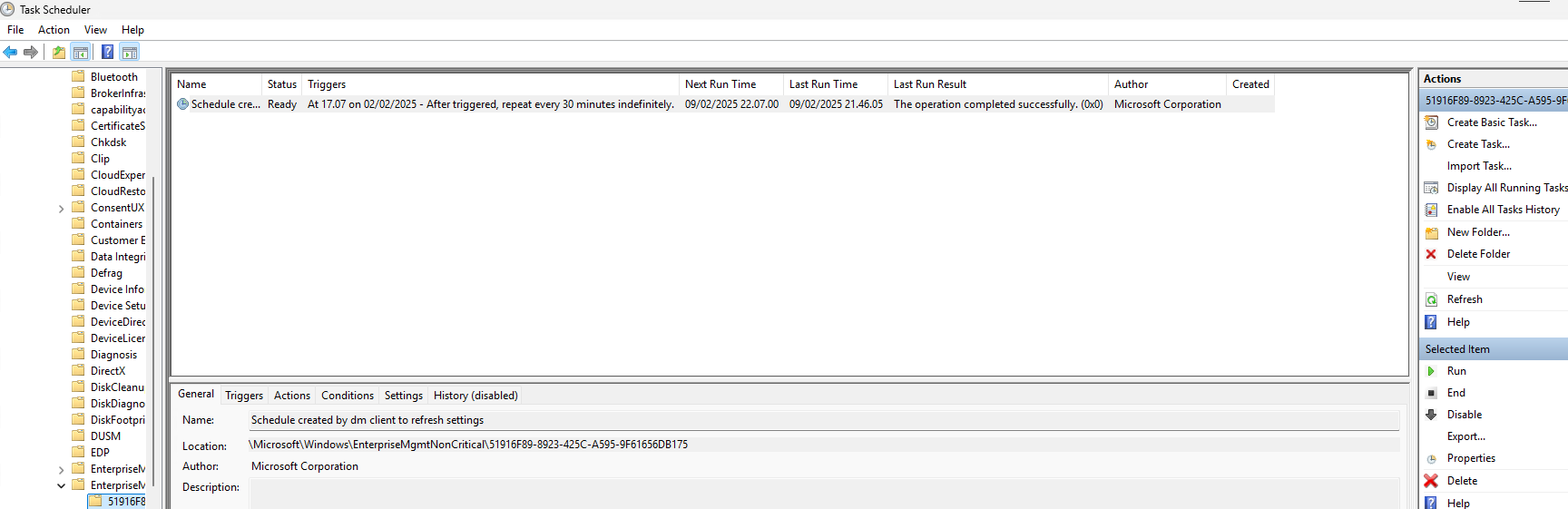
Luckily for us, the Administrator Protection feature is now back in place after Config Refresh has been running!
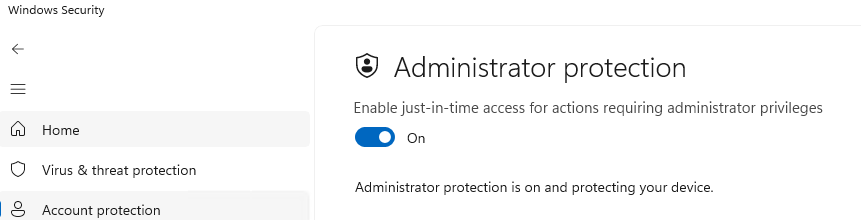
Disable Account Protection View
In order to make it harder for the end-user to disable Administrator Protection, you can hide/disable the tab directly from Intune.
- Go to the Intune portal and navigate to the Endpoint Security tab.
- Under Antivirus, you can create a new policy. Select create new policy and pick Windows and Windows Security Experience.
- Name your policy and click next. Unfold the "Windows Defender Security Center" tab and make sure to change the "Disable Account Protection UI" to "(Enable) The users cannot see the display of the Account Protection area in Windows Defender Security Center".
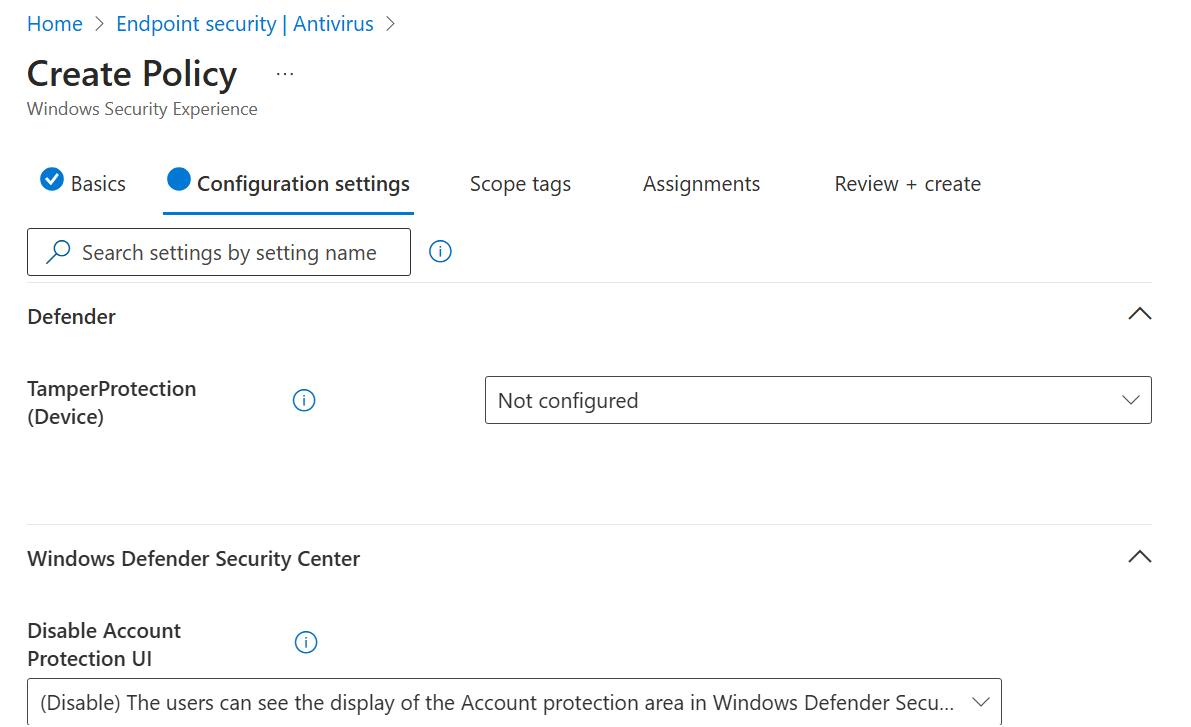
This will make sure that the Account Protection tab isn't available for the end-user within the Windows Security Center.
- Select your assignments and click create policy!
Once the device has checked in with Intune, you can now see that the Account Protection tab isn't visible on the device.
Important Notes
I want to mention some of the important things to remember when you are trying Administrator Protection.
- It utilizes a virtual account when elevating, which can make it difficult to access files in the normal user context.
An example can be that you have an application that needs to access files on a network drive or through another location in the normal user context.
- By default, Administrator Protection can be turned off through the Windows Security Center.
Because the user is an administrator on their device, they can actually go directly into the Windows Security Center and turn Administrator Protection off until next sync with Intune.
However, this can be disabled through the Endpoint Security section in Intune, as shown earlier in this blog.
Conclusion
Thank you very much for reading this blog about Administrator Protection. I hope it gave some insights into this new feature.
